
Techniques to Use Essential Magento 2 Security Headers
43% of cyberattacks target small businesses, with e-commerce stores being prime targets. Without proper Magento 2 security headers, your site is vulnerable to malicious attacks.
The article explores the implementation techniques and essential security headers.
Key Takeaways
-
Essential security headers prevent clickjacking and other web threats.
-
Advanced techniques help automate and modularize your header setup.
-
Test and confirm headers using browsers and Magento-specific methods.
-
Future-proof your header setup as security standards and browser behavior evolve.
-
Uncover real-world challenges in header implementation and how to fix them.
What Overview of Progressive Web App (PWA)
Progressive Web Apps offer the same experience as native apps. It offers improved performance.
Progressive Web Apps blend websites and apps. They stay fast and reliable on any device. PWAs offer:
-
Offline access: Users can view content when offline.
-
Discoverability: PWAs show up well on search engines.
-
Security: HTTPS keeps connections safe for users.
-
Push notifications: PWAs send alerts, even when the user isn’t on the app.
-
Cross-platform: Works on any device without separate apps.
-
Automatic updates: PWAs update without user action, keeping the latest version.
-
Cost-effective: PWA themes for Magento cut building costs for mobile apps.
Using web technologies, PWAs give a good experience that speeds up sites. PWA integration can change your Magento 2 store. It creates an experience for PWA store owners focusing on speed and mobile use.
Introduction and Overview of Magento 2 PWA Theme
A Magento 2 PWA theme allows your store to become a PWA. It provides a fast, app-like experience for the users on mobile and desktop devices.
Magento 2 PWA themes let you add PWA features to your website. You do not need deep technical knowledge. Ready-to-use PWA themes for Magento add features. They include offline access, push notifications, and faster load times. This leads to a good user experience and a faster website.
Magento PWA Studio supports development and maintenance. It creates a Magento PWA that works well on mobile devices.
9 Reasons to Use a Magento 2 PWA Theme
1. Responsive User Experience
PWAs runs on any devices, like tablets or desktops. Magento PWA themes fit your site to various screen sizes. This gives users a good and steady experience. This turns visitors into loyal customers.
2. Fast Loading
PWAs load faster than traditional mobile sites. Depending on optimization, a PWA theme can reduce loading times. It is by 2-5 times compared to traditional mobile sites. This leads to a good browsing experience, especially for mobile users.
3. SEO Benefits
SEO matters for businesses to get noticed online. Magento PWA themes boost SEO by offering faster load times. They also support mobile-first indexing and structured data. This gets your site higher in search results. A site that loads fast ranks better.
4. Smooth Offline Experience
A PWA lets users browse, add items to their cart, and check out without an internet connection. Once they come back online, payments go through. This makes online shopping simple, especially for customers on the go.
5. Cost-Effectiveness
Switching to a new platform can be expensive, but Magento 2 PWA themes cost less. You will not need coding skills and will save money by managing one app. This is a simple and affordable way to move to a PWA website.
6. Interactive
A Magento PWA theme gives users an app-like experience. Customers can save your site to their home screen and receive push notifications. This keeps them engaged and brings them back to your store.
7. Smooth Integration
Magento PWA themes work with your existing website. You can manage both platforms from the same backend, and any changes to your main site will appear on the PWA. This keeps managing your site quick and easy.
8. No Downloads or Manual Updates
Customers can access PWAs without downloading or updating anything. They can add your site to their home screen for access. A Magento PWA means businesses do not worry about updates. This keeps things simple for you and your customers.
9 Easy & Effective Re-engagement
Push notifications bring customers back to your site. PWA themes send updates, promotions, and reminders to users. This builds customer engagement and can drive more sales.
5 Magento 2 PWA Themes: Free and Paid Options
1. Magento PWA Theme by SimiCart
anchor text builds a fast storefront. With over 40 pre-designed templates, it gives an app-like user experience. This theme speeds up your site and online presence.
Key Features:
-
40+ pre-designed templates for a quick setup.
-
Mobile-compatible design for good navigation.
-
An Interface for good user interaction.
-
Preview and publishing process for quick updates.
Pricing: A free, open-source version is available. Its customization costs vary based on requirements.
2. Magento 2 PWA Theme by BSS Commerce
The BSS Commerce Magento 2 PWA theme lifts your store's SEO, traffic, and sales. Its quick page load times and app-like feel make browsing good and fun for users.
Key Features:
-
Lightning-fast page loads for a good user experience.
-
SEO tuned to raise search rankings.
-
Home screen icon for access.
Pricing: Custom pricing based on specific needs.
3. Magento 2 PWA Theme by ScandiPWA
The ScandiPWA Magento 2 theme builds a PWA storefront. It supports more than 350 Magento features. It offers a fast setup and does not need middleware.
Key Features:
-
No middleware for quick setup.
-
Supports over 350 Magento features with many options.
-
Design with flexible options.
-
Tuned for speed.
Pricing: Free, open-source version; paid support costs depend on features.
4. Magento 2 PWA Theme by Onilab
Onilab's Magento 2 PWA theme offers an app-like feel and a tuned user interface. It lifts SEO and gives a good experience, both online and offline.
Key Features:
-
App-like experience for good user engagement.
-
SEO tuned for good rankings.
-
Offline browsing for steady access.
-
Design for navigation.
Pricing: Custom pricing based on project needs.
5. Magento 2 PWA Theme by Tigren
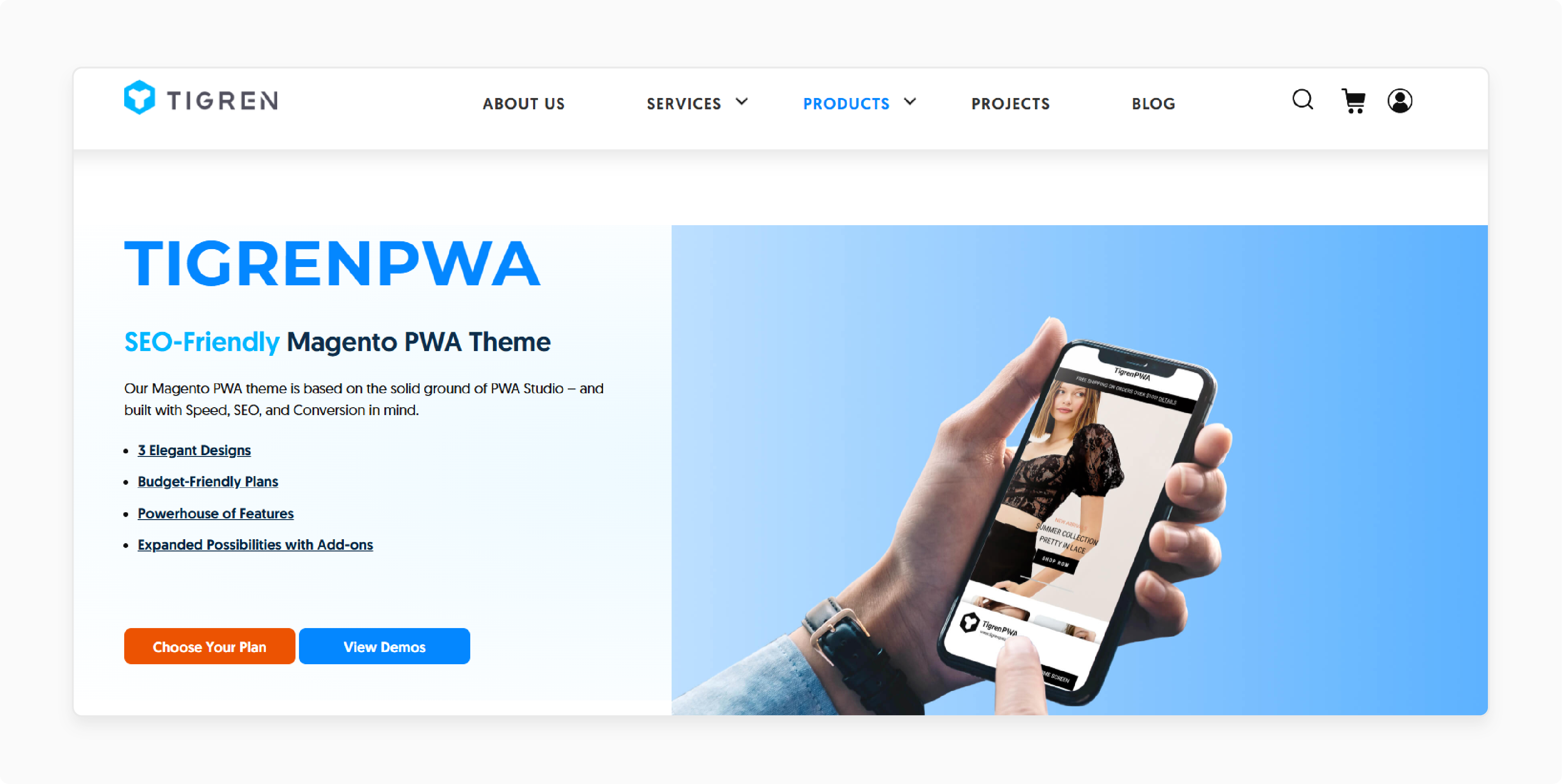
Tigren PWA theme designs for speed, SEO, and conversion rates. These themes, built on PWA Studio, include live chat and one-step checkout. They aim to make shopping better.
Key Features:
-
Tuned for speed and SEO.
-
Live chat and one-step checkout raise conversions.
-
Over 20 add-ons for added features.
-
Free lifetime updates.
Pricing: Starting at $199.
7 Things to Know Before Choosing a Magento 2 PWA Theme
1. Create Listing Requirements
List what your store needs before picking a PWA theme for your Magento. A clear list will keep you focused on the right options.
-
This filters out themes that do not match your goals.
-
Look at how the theme handles speed, design, and navigation.
-
Check it supports sales functions and good browsing.
-
Listing your needs keeps you from choosing themes that miss features.
2. Consider Budget
Theme pricing varies by design, features, and developer support.
-
An open-source PWA theme for Magento offers control but may need more setup.
-
Paid themes like the PWA theme by CedCommerce come with support and updates.
-
Weigh your budget against long-term growth.
-
Check you get value for what you spend.
3. Preview the Demo
Try the demo before choosing a theme. It shows how the PWA Magento theme works on different devices.
-
Check that the theme design loads and looks good on all screens.
-
Demos like the SimiCart or Tigren PWA themes show what’s possible.
-
Choose a ready-made PWA theme that feels good and polished.
-
Test a few Magento 2 PWA themes to find one that fits.
4. Check Customer Reviews
Reading reviews gives you feedback from people who have used the theme.
-
Look at both the positives and the complaints to see the full picture.
-
Watch for recurring problems, like slow load times or bugs.
-
Themes like the SimiCart theme often get good reviews from users.
-
Feedback can point you toward a PWA theme for your store.
5. Ensure Compatibility and Updates
The PWA template should work well with your current setup and future upgrades.
-
The theme should support extensions and provide updates.
-
Look for compatibility with Magento 2 features and tools.
-
Some themes work well with headless Magento setups, so test for that if needed.
-
Updates keep your site secure and working over time.
6. Compare Different Magento Themes
There are many options, and comparing them leads to a good choice.
-
Some developers build themes on Magento, while others derive them from a parent theme.
-
Look at design, speed, and features.
-
Themes built on PWA Studio are stable.
-
A theme will match your design and speed needs.
7. Choose the Right Magento Hosting Provider
Hosting matters for running a fast Magento website with a progressive web app.
-
Your host should support SSL, Varnish caching, and high uptime.
-
Magento-specific requirements like PHP 8.1+, Elasticsearch, and Node.js.
-
A good setup ensures users can add the PWA to their phones or tablets.
-
Look at features that support a working PWA.
5 Key Trends Shaping Magento 2 PWA Themes
| Trend | Details |
|---|---|
| Hybrid Development Approach | More stores are mixing ready-made PWA themes with custom changes. This helps save time and money while giving you the flexibility to adjust. |
| Push Notifications | Push notifications are being used more to bring customers back to your store. They are great for sharing promotions, updates, and new arrivals. |
| Enhanced SEO Capabilities | New PWA themes are focusing on SEO. They are faster, use clean URLs, and make the site rank better in Magento search results. |
| Scalable Architecture | ScandiPWA and Venia help your Magento store grow. They support future updates and new tools without needing a complete overhaul. |
| Offline & Low-Network Support | With better caching, pages load even when the internet is slow or unavailable. This ensures a smoother shopping experience, even on poor networks. |
FAQs
1. What factors should you consider when choosing layout components for your Magento PWA?
Store owners should make their site fit all devices. The design should work well across both mobile and desktop. Navigation should be simple. Speed matters for a good browsing experience. A clean, well-organized layout builds customer loyalty and raises sales.
2. How do plugins enhance the PWA frontend experience?
Plugins add features. They work on search and customer reviews to make the site useful. They let you change the site without starting over. You can connect with payment tools and other services with plugins. This makes the site faster and simpler for customers to use.
3. Are mobile applications developed apart from the main site for Magento 2 PWAs?
With PWA, everything shares one codebase. This means you only manage one version of the site. It works well on both mobile and desktop. This gives a good experience on all devices. Users can update both versions at once.
4. How does a well-structured category system benefit stores on Magento PWA platforms?
A well-organized category system lets customers find what they want. It betters the shopping experience by saving time. It aids search engines in understanding content-raising SEO. This makes products simple to find, which can lead to more sales.
5. Should US store owners add features to their checkout cart for Magento PWA?
US store owners should offer payment options like credit cards and PayPal. This speeds up the checkout process and keeps it convenient. Guest checkout and auto-fill for shipping addresses save time. Offering real-time shipping and tax calculations cuts surprises at checkout.
6. When developing Magento PWA, what should developers consider about versions?
Developers should always use the latest version of Magento. New updates offer better features and security. They also make the site more compatible with modern tools. Planning for future growth and ensuring the site can scale is also important.
Summary
A Magento 2 PWA Theme helps create a faster, app-like experience for website visitors. It improves the site's performance and responsiveness across different devices. Consider the following tips before choosing a Magento PWA development:
-
Create Listing Requirements: Describe your store's needs before picking a theme. This will help you stay focused on the right options.
-
Consider Budget: Think about your budget. Make sure the theme you choose offers good value for the price.
-
Check Customer Reviews: Look at reviews from other users. Take note of both the positive and negative feedback.
Explore managed Magento hosting to simplify the technical management of your PWA site.
[Updated on April 10,2025]


