
What is Magento Malware and How Magento Hosting Protects e-Store?
Magento malware can cause severe damage to your online store, putting customer data and trust at risk. To protect your eCommerce presence, staying alert to security threats and learning to remove them efficiently is important. This tutorial will guide you through removing Magento malware from your online store.
Key Takeaways
-
Regularly update Magento and plugins to prevent vulnerabilities.
-
Implement strong passwords and admin practices for enhanced security.
-
Use security tools like MageReport for malware detection and removal.
-
Employ SSL certificates and firewalls for robust site protection.
-
Engage with security experts for persistent threats and PCI compliance.
What is Magento Malware?
Magento malware is malicious software designed to exploit vulnerabilities in the Magento eCommerce platform. This type of malware can come in various forms, such as viruses, trojans, worms, and spyware.
It can be hidden in website files. It can also be injected into databases. This can cause harm by stealing sensitive information. It can redirect traffic to malicious sites. Additionally, it can install harmful scripts.
How Does Magento Malware Spread?
Magento malware can spread in various ways, including:
-
Outdated software: If you are running an outdated version of Magento, it can contain security vulnerabilities that hackers can exploit.
-
Weak passwords: Using weak or easily guessable passwords makes it easier for hackers to access your store and inject malware.
-
Compromised extensions: Third-party extensions can also be a source of malware, especially if they come from unreliable sources.
-
Phishing attacks: Hackers can also use phishing techniques to trick store owners into giving them access to their website files or databases.
Signs of Magento Malware Infection
There are several signs that your Magento store may be infected with malware, including:
-
Suspicious files: If you notice unusual or unfamiliar files on your server, it could be a sign of malware.
-
Redirections: If your website is redirecting to other sites without your permission, it could indicate the presence of malware.
-
Slow loading times: Due to increased server requests, Malware can slow down your website's performance.
-
Changes in code: If you notice any changes in your website's code that you did not make, it could be a sign of malware injection.
-
Unauthorized orders: Malware can also cause unauthorized orders to be placed in your store, resulting in financial loss.
Consequences of Magento Malware
The repercussions of Magento malware can be severe and multifaceted:
-
Decline in Traffic and Revenue: Malware infections can lead to a noticeable decrease in user traffic as potential customers avoid a compromised store. This inevitably results in lost sales and revenue, undermining the store's profitability.
-
SEO Impact: Search engines are designed to blacklist or lower the rankings of sites that could potentially harm users. This means that malware can cause severe damage to your website’s search engine optimization (SEO). Consequently, it becomes harder for new customers to find your store online.
-
Lack of Consumer Trust: Trust is a cornerstone of online commerce. Suppose customers suspect their data is not secure or has been compromised due to malware. In that case, they will likely avoid your store, amplifying the challenge of attracting and retaining a loyal customer base.
-
Data Sold on the Dark Web: A breach could result in the sale of your site's sensitive data on Onion sites. This can erode competitive advantage and cause significant financial and reputational harm.
-
Sensitive Data Theft: Phishing pages or malicious scripts can directly steal sensitive customer data. This includes credit card numbers and personal information. This escalates the potential for fraud and identity theft.
How Managed Magento Hosting Protects e-Stores
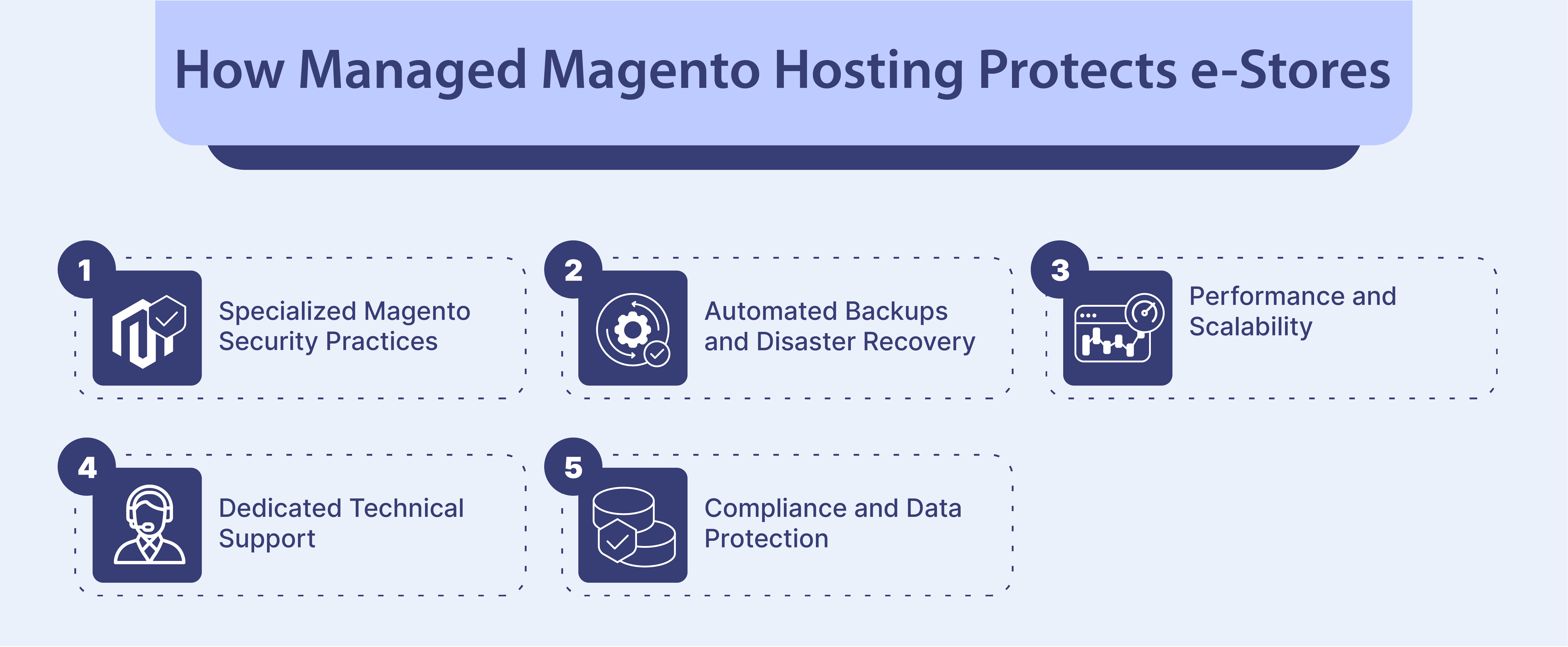
1. Specialized Magento Security Practices
- Proactive Monitoring and Threat Detection: Managed hosting services use continuous monitoring tools. These tools detect and neutralize threats before they escalate. This ensures your Magento store remains secure against emerging vulnerabilities.
- Custom Security Configurations: Security configurations are tailored and optimized for Magento. They help fortify your store’s defenses. This reduces the risk of malware infections. These configurations include specialized firewalls, web application firewalls (WAF), and intrusion detection systems (IDS). They are specifically designed to protect Magento stores.
2. Automated Backups and Disaster Recovery
- Regular, Automated Backups: Automated Magento backup solutions ensure data integrity. They enable quick restoration in the event of data loss or malware attack. Managed hosting providers typically offer off-site backups for added security.
- Disaster Recovery Plans: Strategies for disaster recovery are comprehensive. They are in place to minimize downtime. They ensure a swift return to normal operations after a security incident.
3. Performance and Scalability
-
Optimized Server Configurations: Servers are optimized for Magento. This improves site performance and reduces the attack surface for potential malware exploits. This is thanks to fine-tuned PHP settings, database optimizations, and more.
-
Scalability Solutions: Managed hosting provides scalability options. These options accommodate traffic spikes without compromising security. This ensures your store remains both fast and secure during peak times.
4. Dedicated Technical Support
-
Magento Expertise: You have access to a team of Magento specialists. They can offer guidance on best security practices. They help with configuration and assist in malware removal efforts. This significantly reduces the risk of future infections.
-
Security Patch Management: Managed hosting services keep your Magento store up to date. They do this with the latest security patches and updates. This addresses vulnerabilities promptly to prevent exploitation.
5. Compliance and Data Protection
-
PCI Compliance Assistance: ECommerce stores must adhere to Payment Card Industry (PCI) standards. Managed Magento hosting can help ensure your store meets these requirements. This safeguards customer payment information.
-
Data Privacy Regulations: Hosting providers know global data protection regulations like GDPR. They can help your store comply with these laws. This protects customer data and avoids hefty fines.
Protecting a Site from Persistent Malware Attacks
Implementing the steps mentioned earlier can protect your website against common malware attacks. However, it's important to note that JavaScript can pose a recurring Malware threat to your file system. To fix this, engage experienced developers or solution partners with expertise in handling complex security challenges.
Maintaining PCI compliance is important. To ensure compliance for your ecommerce store, follow these steps:
-
Add a firewall to protect your store
-
Use HTTPS security with an SSL certificate
-
Consider using Magento firewalls for added protection
-
Choose a cloud hosting platform like MGT-Commerce for free domain-level SSL security
-
Implement a security policy that includes regular backups, security monitoring, and a secure payment gateway integration.
FAQs
1. What steps should I take if my Magento 2 plugin is hacked?
Scan your site with a reputable security tool to identify the malware. Next, change all passwords immediately, and update or reinstall any affected plugins and themes to remove any backdoors. Contact Magento security experts for additional guidance on recovery and future prevention.
2. How can I protect my theme from a virus?
Regularly update your themes to patch any known vulnerabilities. Use security plugins to monitor suspicious activity and follow best practices as suggested by experts, such as those from Adobe and Microsoft. Also, ensure you have strong password policies for all user accounts.
3. Is there a way to detect and remove a magecart script?
Monitoring tools can detect unusual activity. This includes unexpected copy-and-paste behavior and post requests, which may indicate a Magecart attack. Removal involves scouring the code for the malicious script. Additionally, I used commands to clean files and update software to close any loopholes.
4. How can I tell if my ecommerce site has been compromised by a trojan?
Look for signs like unauthorized ad displays. Watch out for unexpected performance drops. Pay attention to suspicious activity complaints from users. Utilize specialized security solutions to scan for Trojans. In confirmed cases, consult with a cybersecurity team. Report the breach to the relevant authorities if necessary.
5. What are some important security measures for my Magento store?
Maintain a regular update schedule for all components. Use robust security plugins, restrict administrator rights, conduct session audits, and choose reliable Magento hosting services. Educate your team on security best practices. Prepare incident response plans with the help of cybersecurity experts.
Summary
Removing Magento malware ensures a safe browsing and purchasing experience for your customers, protects sensitive data, and safeguards your brand reputation. Partner with security experts and dedicated Magento hosting providers for optimal protection.



