
Magento 2 Security Scan for Proactive Protection
[Updated July 4, 2025] Want to run a security scan for your store without paying for a pricey tool?
Magento 2 security scan is a free-to-use tool launched officially by Adobe. It helps check vulnerabilities and protect Magento webshops from cyber threats.
This article explores the functionality and setup of the Magento 2 Security Scan tool.
Key Takeaways
-
The Magento Security Scan monitors your store for threats.
-
The scan identifies threats from an outside perspective.
-
Setup requires site verification and a scan schedule.
-
Attackers exploit flaws like XSS and outdated software.
-
Timed updates, backups, and access controls help enhance security
What is Magento 2 Security Scan?
“The Magento 2 Security Scan is a free service from Adobe. It allows merchants to scan their sites for security risks.”
This tool provides real-time insights into a store's security status. It helps merchants protect their business from various threats. It identifies potential weaknesses before they get compromised.
Key functions include:
-
Finding known security vulnerabilities and malware.
-
Checking for outdated or missing security patches.
-
Identifying potential server security misconfigurations.
-
Detecting digital skimming injections and other malicious code.
Store owners receive notifications about all security issues. These alerts help with prompt and quick remediation. The service supports all Magento Commerce and Open Source versions.
This service tracks a store's security posture over time. It maintains historical reports of all scans performed. These reports show successful and failed security checks. Scans run over 21,000 security tests for comprehensive malware detection. This approach safeguards customer data and business operations.
How Does The Magento 2 Security Scan Work?
1. External Signature-Based Scanning
-
The tool sends automated requests to your Magento site. It then analyzes the HTTP responses for specific patterns.
-
It looks for signatures of known malicious code injections. The scanner identifies patterns linked to digital skimming malware.
-
The scan checks for unauthorized JavaScript or iFrame elements. These elements often imply a client-side security compromise.
-
It also verifies the presence of specific security headers. Missing headers can reveal potential server configuration weaknesses.
2. Domain Ownership Verification
-
The scan requires proof of site ownership for security. This process prevents unauthorized scans on any third-party websites.
-
Adobe generates a unique
metatag verification code. You must place this code within your theme's HTMLhead. -
The scanner sends a request to your site's homepage. It then parses the HTML to find the verification code.
-
A successful match confirms your control over the domain. The system then authorizes scheduled and on-demand security scans.
3. Vulnerability Database Cross-Referencing
-
The scan checks your Magento platform for patch levels. It identifies the specific Magento version your site is running.
-
The tool checks your version against a database of known security issues. This database includes documented Common Vulnerabilities and Exposures (CVEs).
-
It checks for missing patches from Adobe Security Bulletins. For example, it checks for fixes related to
APSB25-XXbulletins. -
The system also identifies some vulnerable third-party extensions. The scan flags extensions with open-for-all security flaws.
4. Automated Scan Scheduling and Execution
-
Merchants configure scans to run at scheduled intervals. The tool offers daily/weekly automated scan options.
-
Adobe’s infrastructure manages the scan execution like a cron job. The process runs without depending on your own server's cron.
-
Scans run from various IP addresses for comprehensive analysis. This approach simulates probes from different network locations.
-
The tool allows for on-demand scans outside the schedule. This feature is useful after making significant site changes.
5. Report Generation and Alerting System
-
The scan compiles all findings into a detailed report. The report categorizes issues by severity level (e.g., critical).
-
Each identified issue includes a clear technical description. It also provides actionable steps for remediation and resolution.
-
The system archives all previous scan reports for review. This history helps track security posture improvements over time.
-
It sends email notifications to the configured admin address. These alerts ensure prompt awareness of any new security issues.
Steps to Execute A Magento 2 Security Scan
Step 1. Initial Configuration Steps
-
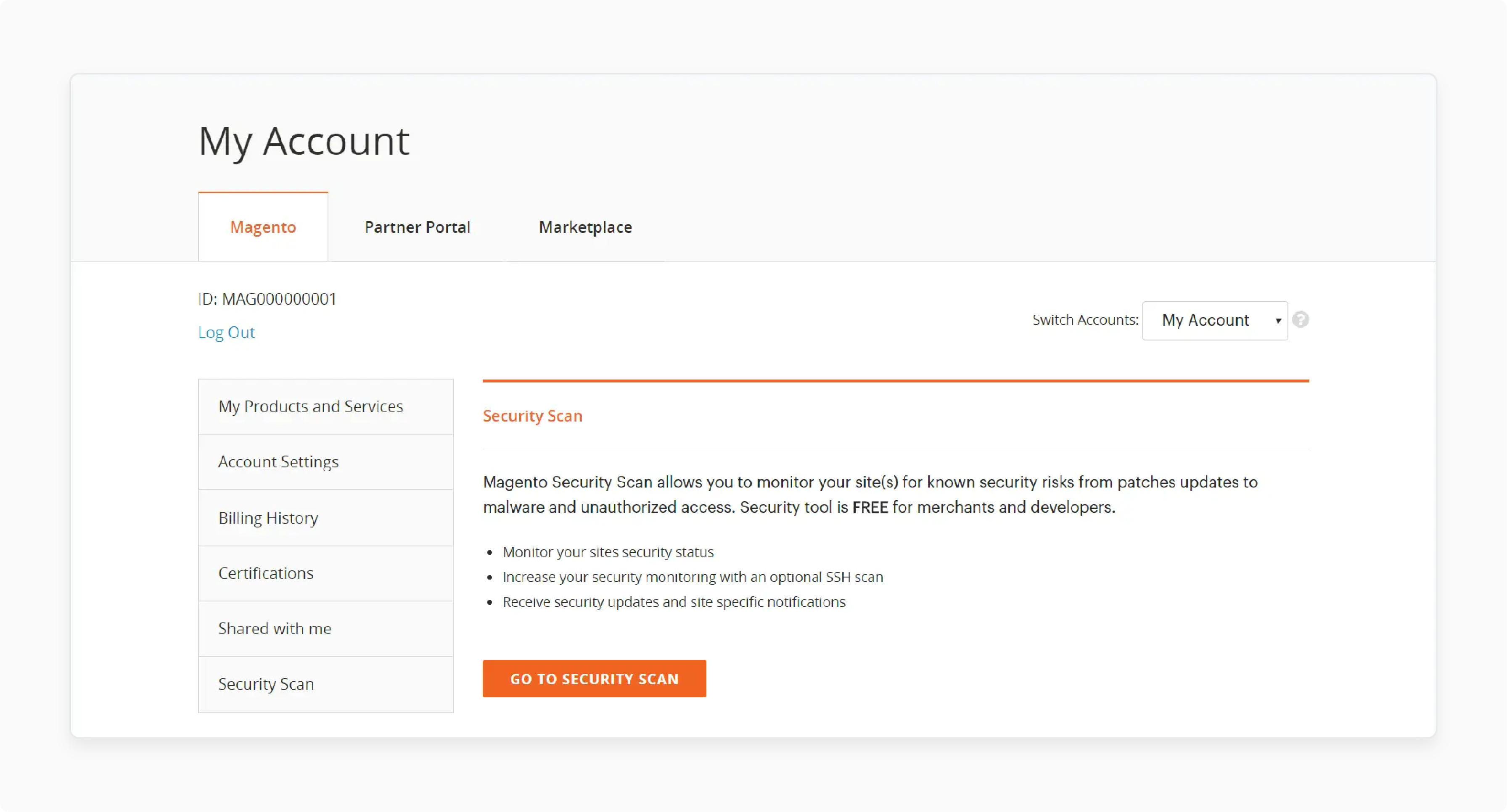
Access Security Scan Dashboard (Users must register for an Adobe ID before proceeding.)
-
Sign in to the Commerce/Magento account portal
-
Navigate to the Security Scan tab location
-
Accept updated terms and conditions
-
Click the "Go to Security Scan" button
-
-
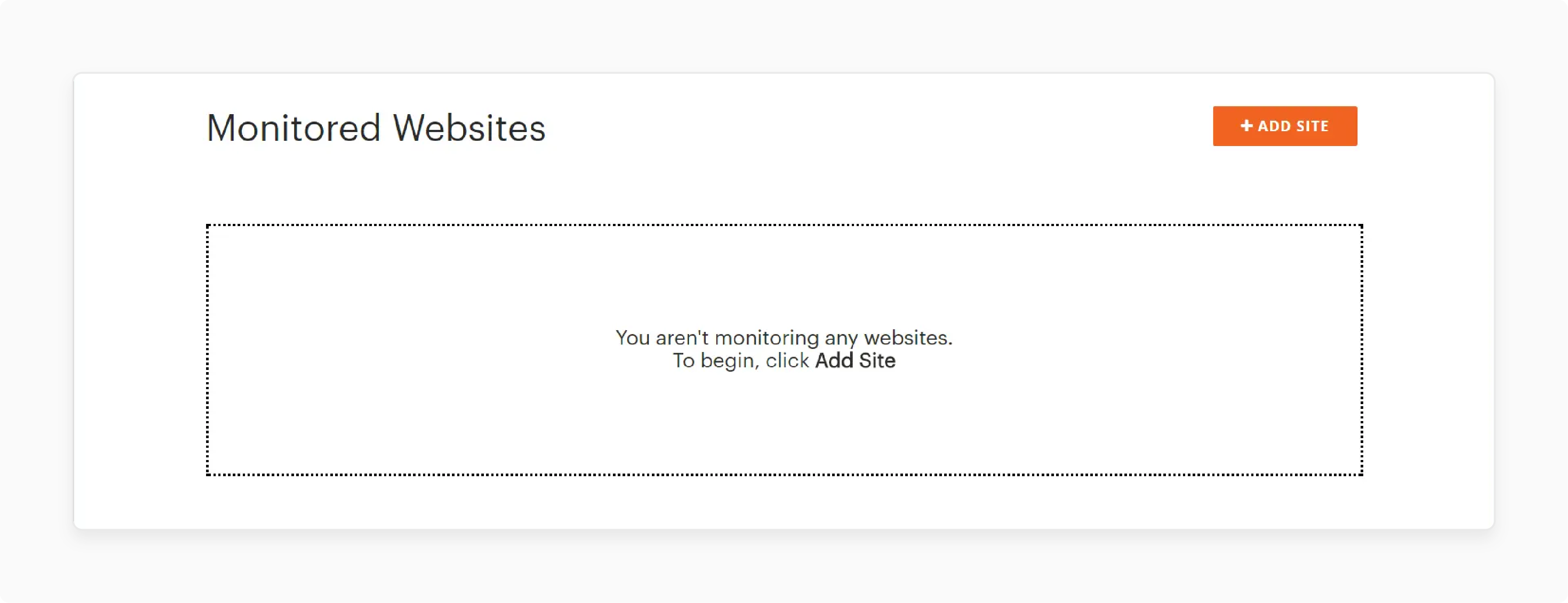
Add Website for Monitoring
-
Select "+Add Site" from the Monitored Websites page
-
Configure separate scans for different domains
-
Enter the accurate Site URL and Site Name
-
Step 2. Domain Ownership Verification
2.1. Commerce Storefront Method
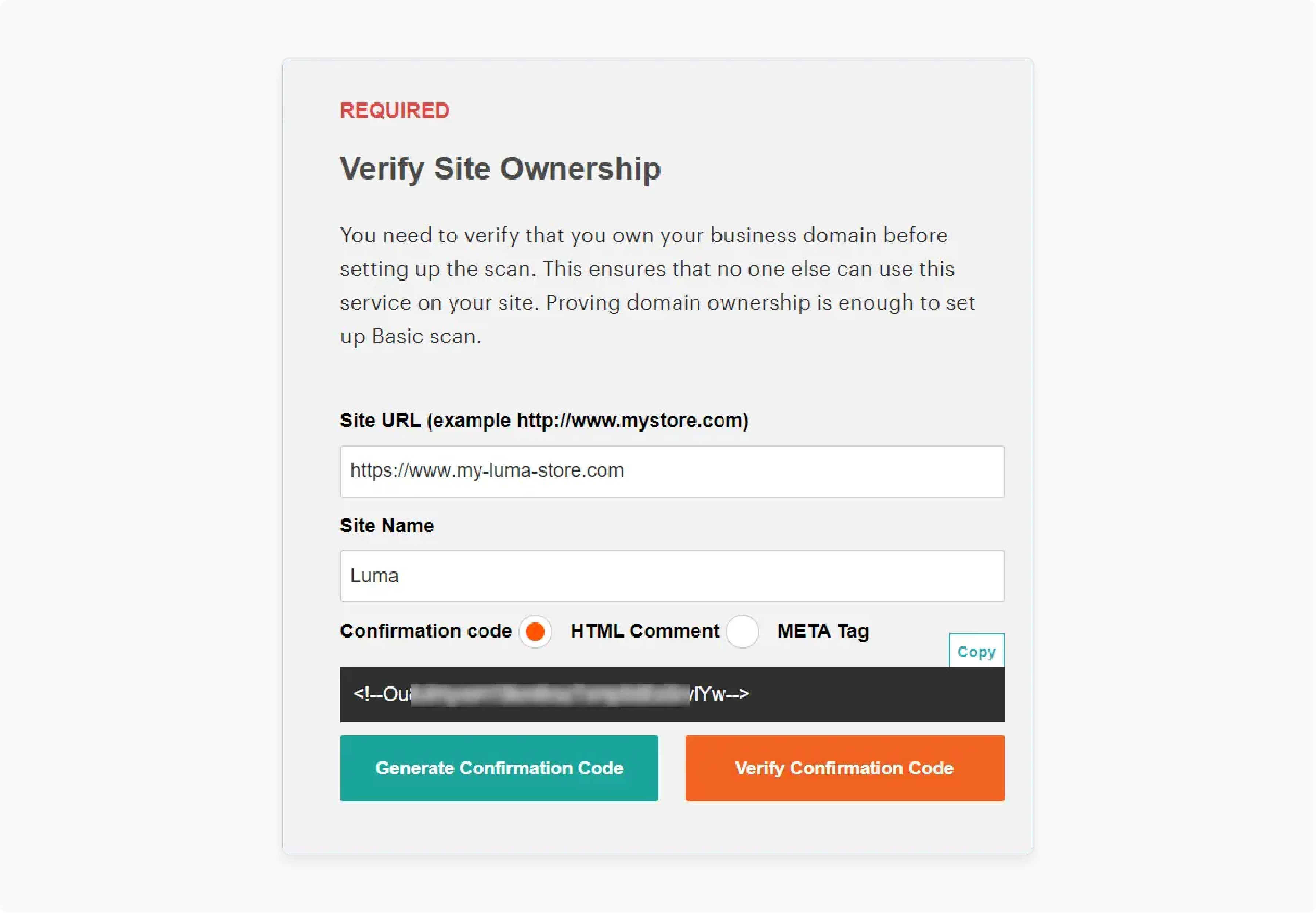
The verification process needs a confirmation code placement within the Admin interface. Generate codes through the Security Scan interface dashboard system.
-
Generate and Copy Code
-
Click the "Generate Confirmation Code" button
-
Copy the generated code to the system clipboard
-
Access the store Admin with full privileges
-
-
Admin Configuration Placement
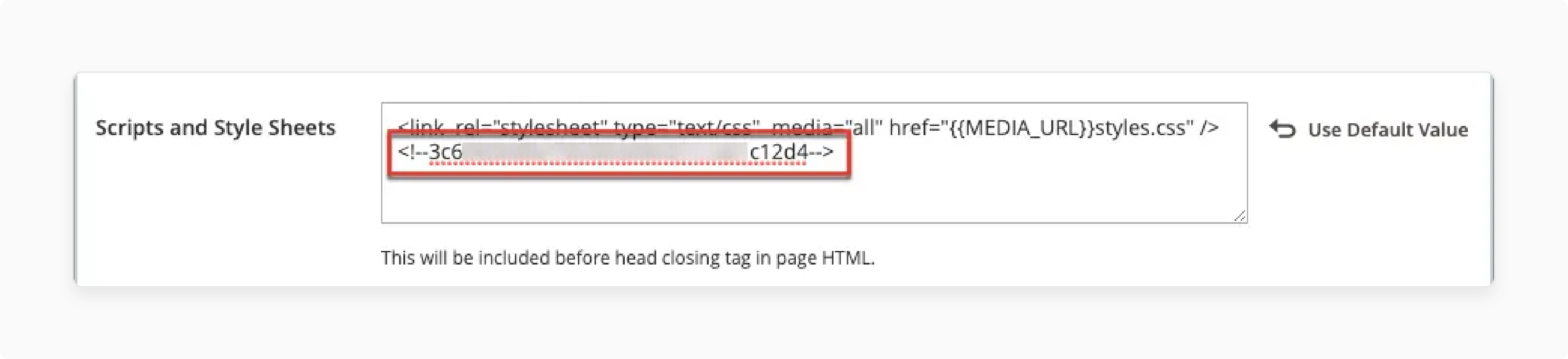
-
Navigate:
Content > Design > Configuration -
Select the target site and click Edit
-
Expand the HTML Head section
-
Locate the "Scripts and Style Sheets" text box
-
Paste the confirmation code into the existing code area
-
Save configuration changes
-
2.2. PWA Storefront Method
PWA implementation uses the META tag confirmation approach for verification. Developers change template files for the ownership verification process.
-
META Tag Generation
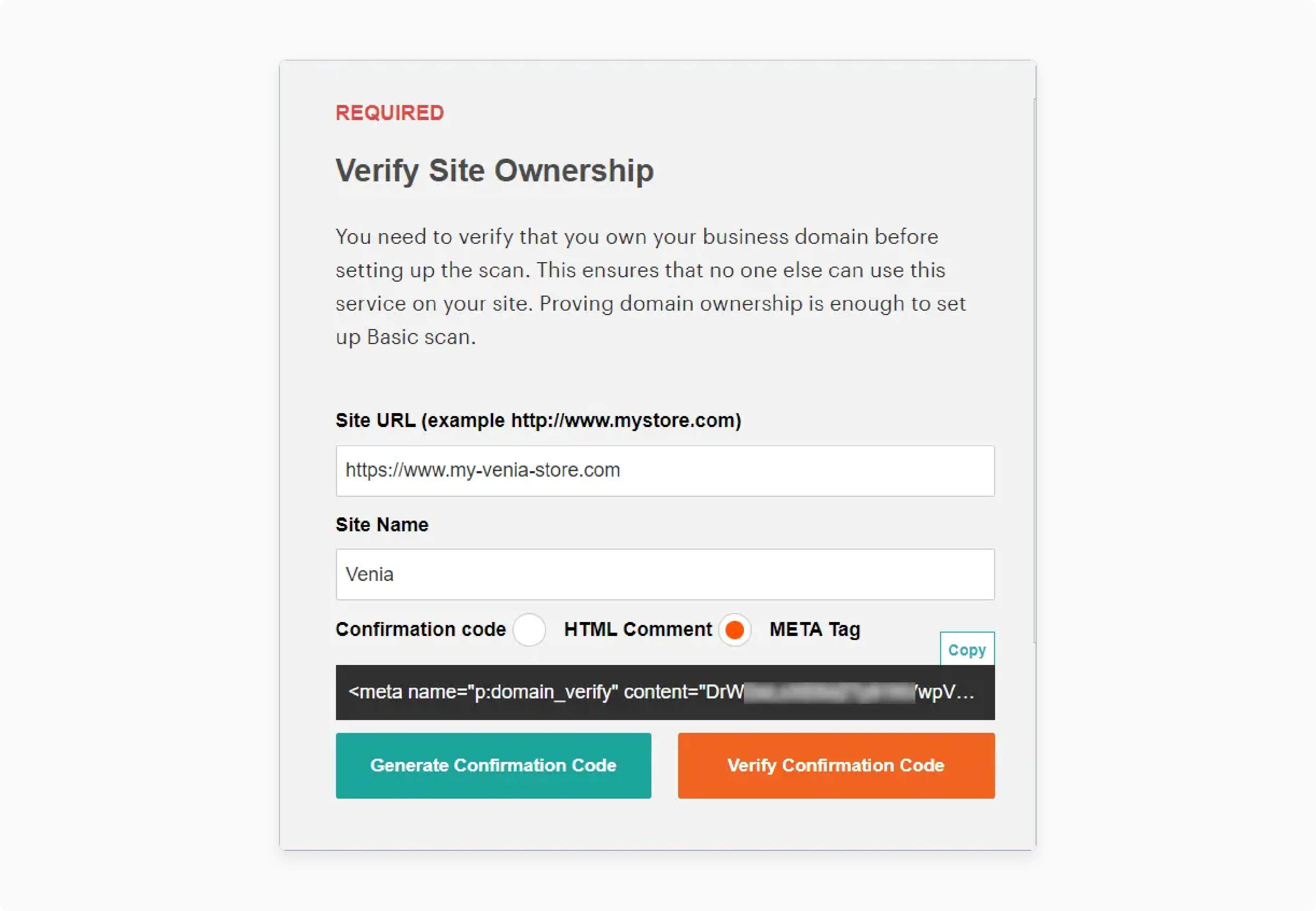
-
Select the META Tag confirmation option
-
Generate and copy the META tag code
-
Access the PWA Studio project directory
-
-
Template File Modification
packages > venia-concept > template.html -
Add the copied META tag to the HTML head
- Save template file changes to the project directory
-
Build and Deploy Process
yarn install && yarn build mkdir pwa && cp -r <path>/dist/* pwa git add . && git commit -m "Added storefront file bundles" && git push origin
Step 3. Scan Configuration Options
3.1 Schedule Configuration
-
Week-by-week Scanning (Recommended)
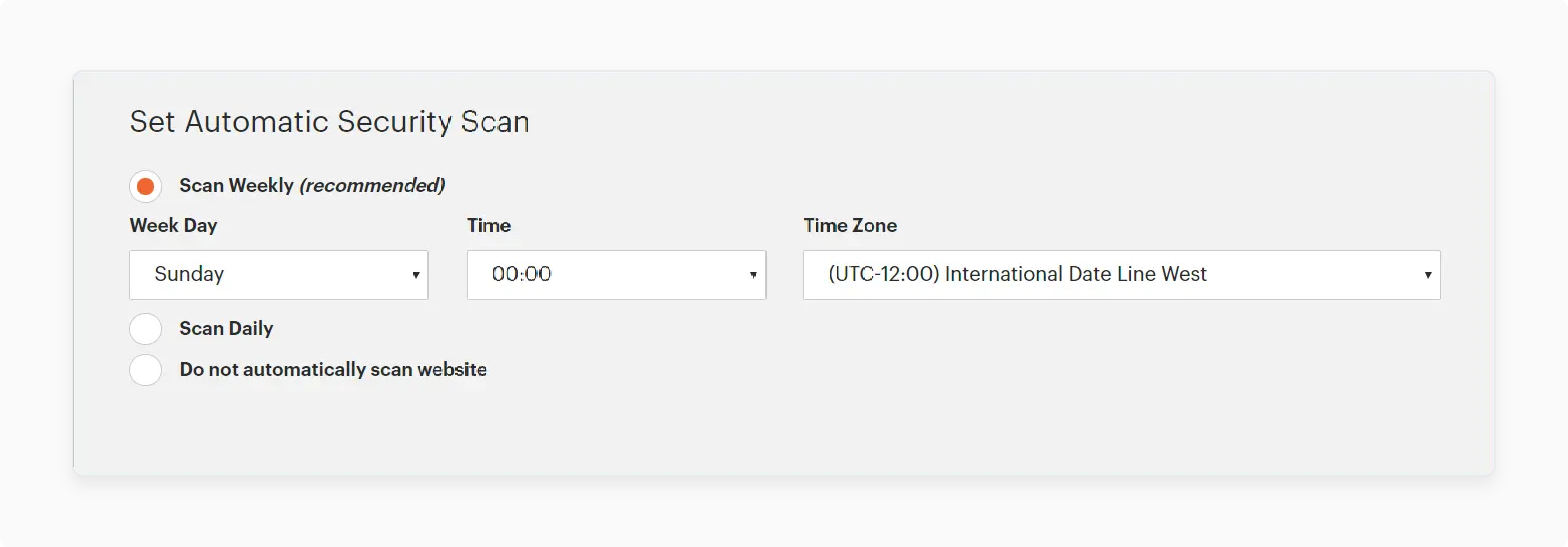
-
Select a specific weekday for execution
-
Configure time and timezone settings
-
Default: Saturday midnight UTC execution
-
-
Day-to-day Scanning
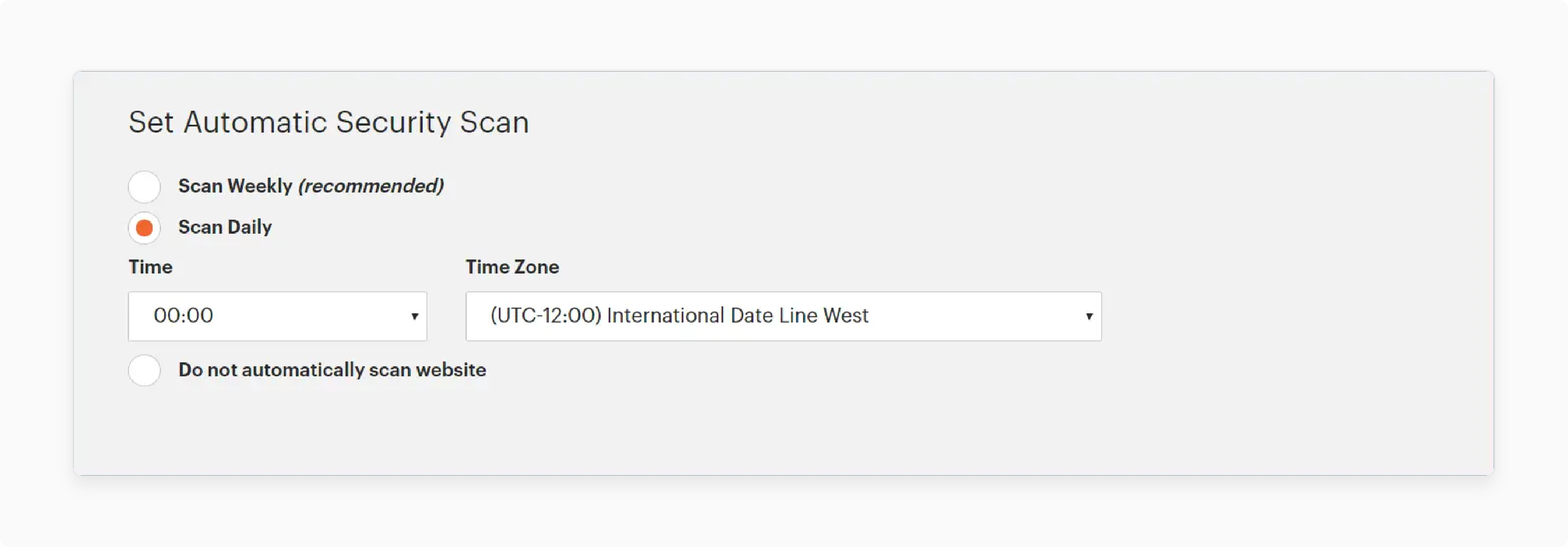
-
Choose the execution time preference for scan operations
-
Set the appropriate timezone for the everyday operations schedule
-
Default: Midnight UTC start time for scanning
-
3.2 Notification Setup
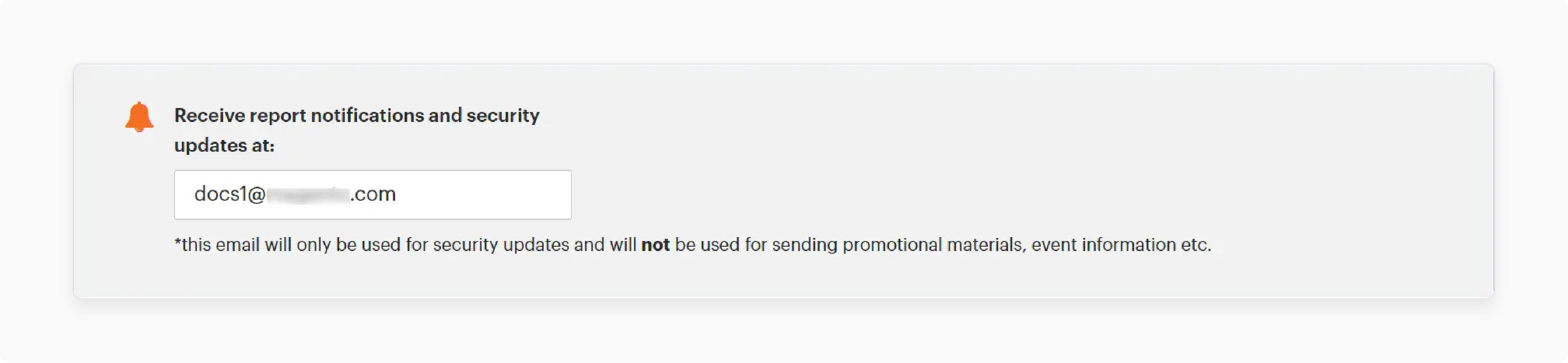
-
Enter your email address for scan notifications and updates. Configure security update alerts for monitoring teams and stakeholders.
-
Submit the configuration after completing all required settings.
Step 4: Verification and Monitoring
-
Return to the Security Scan page interface within the account dashboard.
-
Click "Verify Confirmation Code" for domain establishment and ownership. Verification adds sites to the monitoring list for tracking.
-
Several websites demand individual configuration processes for each domain.
2025's Common Magento Security Vulnerabilities
| Vulnerability Type | Description | Affected Versions (Example) | Common Exploits |
|---|---|---|---|
| Cross-Site Scripting (XSS) | Attackers inject bad scripts into web pages. Users then view these malicious web pages. | Adobe Commerce & Magento Open Source 2.4.8 and earlier. | Stealing user sessions and personal data. Redirecting users to dangerous fake sites. |
| Improper Authorization | Users access restricted areas without permission. They can perform actions they should not do. | Adobe Commerce & Magento Open Source 2.4.7-p5 and earlier. | Gaining access to private data without approval. Getting higher user permissions on the site. |
| Security Bypass | Attackers get around the site's security rules. They gain access that they should not have. | Adobe Commerce & Magento Open Source 2.4.8 and earlier. | Entering private admin sections of the store. Changing important store settings without approval. |
| Privilege Escalation | A user with low access gains higher access. They could become a website administrator. | Adobe Commerce & Magento Open Source 2.4.8 and earlier. | Taking complete control over the entire website. Stealing sensitive customer or business data. |
| Outdated Software Components | This is using old Magento or extension versions. These old versions have known security problems. | All unsupported Magento versions. | Attackers use known and published security flaws. These security flaws have not been patched yet. |
5 Tips to Enhance Magento Store Security
1. Core Platform and Dependency Management
-
Update the Magento core with Composer commands. The command
composer require magento/product-community-edition 2.4.8sets the version. -
Run
composer updateto get security patches. This command pulls the needed software package versions. -
Review third-party extensions for known vulnerabilities. Remove or replace any compromised or abandoned modules.
-
Apply hotfixes using
magento-cloud-patcherfor cloud users. This tool applies specific patches from Adobe.
2. Admin Access Control Hardening
-
Make sure all admin users use Two-Factor Authentication (2FA). 2FA is mandatory in Magento 2.4.x.
-
Change the default admin URI to a secret path. Set
backend/frontNamein theapp/etc/env.phpfile. -
Enforce IP-based access for the admin panel. Configure Nginx or Apache for IP whitelisting.
-
Create specific admin roles with the least privilege. Assign users the permissions needed for their tasks.
3. Server and Filesystem Security
-
Set file and directory permissions on your server. Use
644permissions for your store files. -
Use
755permissions for all site directories. Avoid777permissions, they grant full access. -
Protect the
app/etc/directory with read-only permissions. This prevents attackers from changing core configuration files. -
Select hosting that supports modern security features. Your host provides firewalling and malware scanning.
4. Network and Application Layer Defense
-
Deploy a Web Application Firewall (WAF) at the edge. A WAF blocks SQL injection and XSS attacks.
-
Set up the WAF to block bad HTTP requests. It checks traffic before it gets to your app.
-
Install an SSL/TLS certificate so your site uses HTTPS. This makes data between users and your site secure.
-
Turn on HSTS headers. This makes browsers always use HTTPS when connecting to your site.
5. Data Integrity and Disaster Recovery
-
Schedule automated backups for files and the database. Use a shell script or a hosting feature for this.
-
Store critical backups in a secure off-site location. This protects your data from server breaches.
-
Test your store's entire backup restoration process. A tested process ensures a swift site recovery.
-
Maintain a disaster recovery plan for incidents. This plan outlines steps for normal store operations.
FAQs
1. How does the free Magento security scan differ from a penetration test?
The Adobe scan is an automated vulnerability checker. It looks for known threats and missing security patches. A penetration test involves manual expert hacking attempts. It uncovers unknown and complex system security flaws.
2. Can the security scan detect all possible vulnerabilities?
The scan cannot find every single security vulnerability. It identifies known issues and common security misconfigurations. Custom code flaws need a separate manual code audit.
3. Does the Adobe security scan find zero-day threats?
This scan does not detect unknown zero-day vulnerabilities. It checks against a database of known threat signatures. A WAF offers much better zero-day threat protection.
4. What are false positives in a Magento security scan?
A false positive is any reported vulnerability that is not present. The scanner can misinterpret custom code as a threat. A developer must review these specific alerts for confirmation.
5. Does the scan tool fix the issues that it finds?
The tool only reports security issues and recommends fixes. It cannot apply patches or change any code on its own. Developers must perform all the remediation steps themselves.
6. Does the security scan ensure PCI DSS compliance?
This scan helps with some important aspects of PCI DSS. It does not guarantee full compliance for your store. PCI compliance requires a much broader set of security controls.
Summary
Magento 2 security requires a proactive and layered approach. Developers need to strengthen security to keep all store assets safe. Below mentioned are the article’s main points
-
Activate the free Adobe Security Scan for your store. Schedule automatic scans for a weekly security check.
-
Install the latest Magento security patches and updates. Update third-party extensions to their newest versions.
-
Secure admin access with a custom URL and 2FA. Use IP whitelisting to limit all admin panel access.
-
Set the correct server file and folder permissions. Use a Web Application Firewall for network protection.
-
Make backups of all your site files and databases. Store these backups in a secure, off-site location.
Consider Managed Magento Hosting for an all-inclusive site audit and protection.
[Updated July 4, 2025]


