
9 Magento Security Best Practices to Protect Your E-commerce Store
Following Magento security best practices lets store owners safeguard their e-commerce store and ensure its safety from potential threats. A secure website and infrastructure are less likely to be targeted by malicious attacks. It ensures the safety of the solution and customers' sensitive information.
Additionally, it reduces the risk of security incidents that can lead to site disruptions and expensive investigations. This article highlights some of the most crucial security practices that should be implemented in your Magento store.
Key Takeaways
-
Delve into 9 best practices for securing your Magento e-commerce store.
-
Learn how to protect your store against potential threats and malicious attacks.
-
Reduce the risk of security incidents that can disrupt site operations and lead to costly investigations.
-
Create a secure environment for your customers' sensitive information.
-
Learn how to respond to security incidents and minimize their impact on your store.
9 Best Magento Security Practices for Your Online Store
1. Enable Two-factor Authentication for Admin and SSH Connections

The Adobe Commerce Admin allows you to manage your store, orders, and customer data. To ensure data security, all users must go through an authentication process to verify their identity before accessing the Admin. Unauthorized access to your data is prevented through this verification process.
Two-factor authentication is used to generate website access codes within a single app. This adds an extra layer of protection to your user account, preventing unauthorized access in case of a lost password or a bot attempting to guess it. For instance, Google Authenticator can generate codes for your store's Admin, your Commerce account, and your Google account.
Enabling MFA on a project necessitates an authentication process for all Adobe Commerce on cloud infrastructure accounts with SSH access. To gain entry to the environment, you must provide either a 2FA code or an API token and SSH certificate.
Through the Adobe Cloud Certifier API, MFA enables users to exchange an OAUTH access token for a temporary SSH certificate. Adobe Commerce on cloud infrastructure generates the SSH certificate if the user has the Admin or Contributor role and valid credentials (SSH key, TFA code, or API token). The certificate expires in one hour but automatically refreshes during the session.
To generate the SSH certificate, users must utilize the Magento-cloud CLI after logging into a project with MFA:
magento-cloud ssh-cert:load
The command ssh-cert:load creates an SSH certificate and installs it in the local user's SSH agent.
2. Secure the Admin

Setting up a custom admin URL to enhance security is recommended rather than using the default "admin" or common terms like "backend." This reduces the risk of unauthorized access attempts by malicious scripts.
To enhance admin security:
-
Add a secret key to URLs.
-
Make passwords case-sensitive.
-
Limit Admin session length, password lifetime interval, and login attempts.
-
Configure keyboard inactivity time before the session expires.
-
Require case-sensitive username and password.
-
To safeguard the Admin from automated brute force attacks, it is recommended that ReCAPTCHA be activated.
-
When assigning Admin permissions to roles and roles to Admin user accounts, it is advisable to follow the principle of least privilege.
3. Restrict Access by IP Address

To enhance the security of your admin panel, you can limit access based on IP addresses. By doing this, only users from specific IPs can enter, reducing the chances of unauthorized access. To limit access based on IP address, make changes to the .htaccess file located in the pub/ directory of your Magento installation. You must add the following lines, replacing ALLOWED_IP_ADDRESS with the IP addresses you wish to authorize.
<FilesMatch "index.php">
Order deny,allow
Deny from all
Allow from ALLOWED_IP_ADDRESS
</FilesMatch>
Regularly update this list of IP addresses, as your team members' IPs may change over time or when they work remotely.
4. Maintain a Secure Site and Infrastructure
-
Block unauthorized access: Collaborate with your Magento hosting partner to establish a VPN tunnel, safeguarding the commerce site and customer data from unauthorized access. Employ an SSH tunnel to prevent unauthorized access to the Commerce application.
-
Use a Web Application Firewall: Detect unusual traffic patterns, like credit card data being sent to unfamiliar IP addresses, with the help of a Web Application Firewall. Adobe Commerce setups on cloud platforms can leverage the integrated Fastly services for built-in WAF functionality.
-
Configure advanced password security settings: Ensure your passwords are strong and update them every 90 days, as the PCI Data Security Standard advises.
-
Use HTTPS: Launching the entire site with HTTPS is crucial for newly implemented Commerce sites. It is a ranking factor for Google and instills trust in users who prefer secure websites for online purchases.
-
Run security scans: Monitor your Adobe Commerce and Magento Open Source sites for security risks and malware using the Commerce Security Scan service. Stay updated with patch releases and security notifications by signing up.
5. Ensure Extensions and Custom Code Security
-
Select a security-savvy partner or solution integrator (SI): Choosing organizations that prioritize secure development practices is important to ensure secure integrations and delivery of custom code.
-
Use secure extensions: To ensure secure and appropriate extensions for Commerce deployments, consult your solution integrator or developer. Use extensions only from the Adobe Commerce Marketplace or through the solution integrator, ensuring the extension license is transferrable. Reduce risk exposure by limiting the number of extensions and vendors. Before integration, review the extension code for security. PHP extension developers should adhere to Adobe Commerce guidelines, processes, and security best practices. They should avoid PHP capabilities that may lead to remote code execution or weak cryptography.
-
Audit code: Check your server and source code repository for any leftover development artifacts. Make sure that log files, .git directories, SQL tunnels, database dumps, php info files, or any other unprotected files that are not necessary are not accessible or publicly visible. These files could potentially be exploited in an attack.
6. Upgrade to the Latest Release
 Adobe regularly releases updated solution components to enhance security and protect customers against potential compromises.
Adobe regularly releases updated solution components to enhance security and protect customers against potential compromises.
To protect against security threats, the first and most effective step is to upgrade to the latest version of Adobe Commerce. Ensure that all installed services, extensions, and patches are current.
Commerce usually provides security updates every quarter, but they may also release quick fixes for significant security risks based on priority and other considerations.
7. Maintaining PCI Compliance
Ecommerce stores that handle credit card transactions must prioritize PCI compliance. Following PCI standards, you safeguard your customers' payment details and maintain their trust in your store. To ensure PCI compliance, take these steps:
-
Use the Latest Version of Magento: To maintain the security of your store, it is crucial to use the latest version of Magento. This ensures you have the most up-to-date security patches to protect your store. Upgrade to the latest version of Magento for enhanced security.
-
Encryption Keys: To safeguard sensitive data stored in the database, Magento 2 utilizes encryption keys. Ensure regular management and rotation of encryption keys to uphold the security of customer data.
-
Secure payment gateway: To safeguard customer payment information during transactions, it is crucial to have a secure payment gateway that complies with PCI standards. This is especially vital for ecommerce websites, as they handle sensitive customer data during checkout.
-
Magento Security Extensions and Services: Enhance the security of your store by using Magento-specific security tools and services. Scan your store for vulnerabilities with the Magento Scan Tool. Prevent spam and bots by implementing Magento reCAPTCHA. Consider hiring a professional service to conduct an audit for your online store.
8. Know the Magento 2 Security Extensions and Tools
a. Magento Security Scan Tool
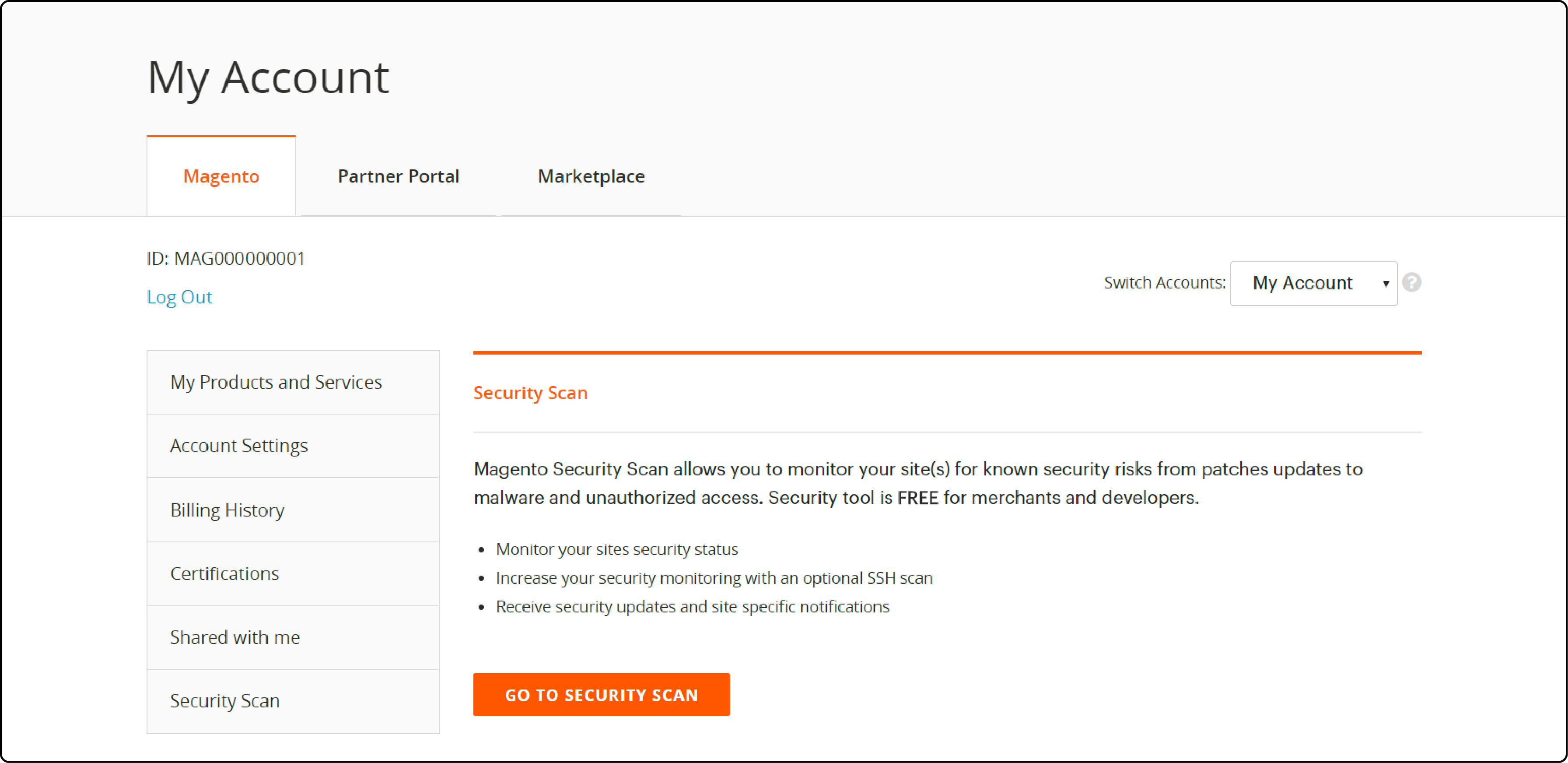
The Magento Security Scan Tool is essential for monitoring and protecting your Magento store. This free tool enables easy scanning for security risks, malware, and unauthorized access. It also provides timely notifications for new vulnerabilities. Detailed reports help address website security issues. Stay proactive in safeguarding your Magento store with this powerful tool.
b. Web Application Firewall
A Web Application Firewall (WAF) is a vital security tool that shields your Magento store from threats. It defends against common web-based attacks like SQL injection, cross-site scripting (XSS), and distributed denial-of-service (DDoS) attacks.
By implementing a WAF, you can safeguard your Magento store, monitor incoming traffic, block malicious requests, and ensure optimal performance even during peak traffic or DDoS attacks.
c. Magento reCAPTCHA
Magento reCAPTCHA is a vital security tool that defends your store's forms against spam and bots. By integrating this feature, you can protect your contact, registration, and review forms from automated spam.
It also improves the user experience by preventing spam from cluttering your site. Moreover, it safeguards customer data integrity and protects it from unauthorized access. Implementing Magento reCAPTCHA is a simple yet effective way to secure your store and provide a pleasant shopping experience for your customers.
9. Responding Against Malware Attacks

Threat actors continuously devise new methods to extract credit card details and personal information from transactions. Here are some common categories of attacks that Adobe Commerce recommends customers to be aware of and protect against:
-
Site defacing: Attackers modify the appearance of a website, compromising access but usually leaving payment information secure.
-
Botnets: Customers' servers become part of a botnet, potentially causing spam email issues or participating in DDoS attacks.
-
Direct server attacks: Data compromise, installation of malware, and disruption of site operations can occur.
-
Silent card capture: Intruders install hidden malware or modify checkout processes to collect credit card data for sale on the dark web.
-
Silent keylogging: Threat actors gather admin user credentials through keylogging code, allowing undetected attacks.
In the event of a security incident impacting your Adobe Commerce on a cloud infrastructure project, follow these critical steps first:
-
Audit all admin user account access.
-
Enable advanced multi-factor authentication (MFA) controls.
-
Preserve critical logs.
-
Review security upgrades for your version of Adobe Commerce.
-
Engage system integrator and security personnel for investigation and remediation efforts. Determine the scope of the attack, identify the attack vector, and take necessary actions such as wiping and reinstalling, removing unnecessary files, and resetting all credentials and keys.
The next step in incident analysis is to gather relevant facts quickly. Adobe Commerce offers several tools for incident analysis, including Audit Admin Action Logs, Observation for Adobe Commerce, and New Relic Logs. These tools provide detailed information and analysis capabilities to help identify the root causes of incidents and ensure optimal performance.
A few other practices you need to take here are:
a. Audit accounts, code, and database
This checklist outlines the steps for auditing admin user accounts, code, and database configuration and logs.
Key tasks include reviewing and removing old or suspicious accounts, rotating passwords, verifying security settings, checking code integrity, and securing the database. Ongoing monitoring and log review are emphasized to detect any signs of compromise.
b. Remove Google Warnings
If Google identifies a website as having malicious code, requesting a review after cleaning the site is important. Reviews for malware-infected sites usually take a few days. Once Google confirms the site is clean, search results and browser warnings should vanish within 72 hours.
c. Review Malware Results Checklist
If malware scanning tools that are accessible to the public validate a malware attack, it is important to investigate the incident. Collaborate with the solution integrator to remove the malware from the website and adhere to the suggested remediation process.
d. Conduct additional reviews
When facing complex attacks, it is advisable to collaborate with skilled developers, external experts, or solution integrators. This collaboration helps restore the website and assess security practices thoroughly.
FAQs
1. What are the best practices for Magento security?
Magento security involves a combination of techniques, including secure coding, applying the latest security patches, using strong authorization, setting correct file permissions, using SSL certificates for secure data transmission, and implementing server hardening measures. Reviewing the Magento security guide for comprehensive tips and resources is recommended.
2. How does a security breach impact an ecommerce site?
A security breach on an ecommerce site can lead to fines and penalties. It can be due to non-compliance with data protection regulations to reputation damage that can turn away potential customers. Furthermore, a breach can disrupt operations, affecting inventory, sales, and shipping processes.
3. How can store owners enhance Magento's security measures?
Store owners can enhance Magento's security by using a trusted hosting provider, incorporating a security plugin, conducting regular penetration testing, and backing up data regularly. Employing Captcha for admin login and subscribing to Magento's security notifications can further bolster the site's defenses against hackers.
4. How can access control measures protect my ecommerce store?
Only trusted admin users can access sensitive parts of your site by implementing an access control feature. Hence, you can significantly reduce the platform's vulnerability to attacks. This involves a mix of secure passwords (a combination of uppercase and lowercase letters, numbers, and symbols) and limiting the number of admin accounts.
5. Are there any specific Magento security features I should know?
Magento offers several built-in security features, such as two-factor authorization, secure FTP, SSL certificates, and a robust access control system. It also regularly releases security fixes to address potential vulnerabilities. Being part of the Magento community helps to stay aware of new security enhancements.
6. What is the importance of having SSL certificates for my ecommerce store?
SSL certificates are crucial for any ecommerce store as they encrypt credit card information and other sensitive data during transmission, providing a safe browsing experience for users. Moreover, having a valid SSL certificate boosts your site's reputation, contributing to better search engine rankings and enhancing customers' trust in your brand.
7. What security extensions are available for Magento ecommerce sites, and how do they protect against hacker attacks?
Magento security extensions are software applications designed to enhance the security of ecommerce platforms. For example, some Magento extensions monitor for suspicious admin access activity, provide backup solutions, and restrict permission to sensitive parts of the store. They offer an added layer of protection against hacks by reinforcing login security, detecting potential vulnerabilities, and conducting regular security reviews.
8. What are the top recommended practices for managing backups and why are they crucial for store security?
Backups are critical to store security, safeguarding valuable content in case of any mishaps or cyber-attacks. Top recommended practices include conducting backups regularly, ensuring backups are saved in different media types and secure locations, and testing restored data for integrity.
Regular backups ensure that even in the event of a compromise, your ecommerce platform can quickly recover with minimal loss of information.
9. Why keep my Magento software and associated applications up-to-date with the latest versions?
Keeping your Magento ecommerce store and its associated applications up-to-date is essential for security reasons. Developers constantly release updates to fix security vulnerabilities, add new features, and improve performance. Running old versions exposes your store to known vulnerabilities that hackers can exploit.
Regular updates are a critical security practice to protect your ecommerce store. It's also worth noting that updated software often has better support from the developers and the community, providing you with quicker solutions when needed.
10. How does a security policy impact the security of a Magento domain, considering security extensions and browsers?
A comprehensive security policy plays a pivotal role in protecting a Magento domain in several ways.
-
First, it establishes protocols for managing user credentials, enforcing strong passwords, and controlling access rights, drastically minimizing unauthorized access.
-
Second, it outlines how and when to apply security extensions, expanding the security features of the Magento platform and closing loopholes in the system.
-
Third, it dictates the conditions for browser interaction with the store. This includes requiring secure (HTTPS) connections and implementing Content Security Policies (CSPs) to protect against cross-site scripting (XSS) attacks.
-
Finally, it guides the conduct of regular security audits, penetration testing, and immediate application of patches to vulnerabilities. Consequently, a well-crafted security policy is a multi-faceted defense mechanism, enhancing the security of the Magento domain on many fronts.
Summary
Magento security best practices form the cornerstone of a secure e-commerce environment. A comprehensive security policy, regular updates, and the responsible management of user credentials and extensions can significantly mitigate risks.
Every Magento store should adhere to these best practices to ensure the safety of their business and customers. Selecting the right Magento-managed hosting provider and regularly monitoring for threats is essential for maintaining a secure Magento domain.



